
Daoyuan Wu (吴道远)
Assistant Professor
Division of Industrial Data Science (DIDS)
School of Data Science, Lingnan University, Hong Kong
Email: daoyuanwu[-]ln.edu.hk; dywu[-]ie.cuhk.edu.hk
Gmail: daoyuan0x
OpenReview |
ORCID |
DBLP |
Scholar
I am currently a tenure-track Assistant Professor at the School of Data Science, Lingnan University (LU), where I lead the AIS2Lab (Artificial Intelligence and Systems Security Lab): https://ais2lab.github.io. Previously, I was a member of the Cybersecurity Lab at HKUST, Cyber Security Research Centre (CYSREN) at NTU, Laboratory for Applied Security Research (LASR) at CUHK, Secure Mobile Center (SMC) at SMU, and The Internet Infrastructure and Security Group at PolyU.
I am always looking for students with persistence in AI/LLM;Blockchain/GPU/MedicalSoftware;PL/Fuzzing to join AIS2Lab.
Positions available: I currently have one PhD student quota and several external/internal grants to support PhDs/RAs (15K)/PostDoc (28K-48K). Please contact me if you are self-motivated, hard-working, and aiming for an academic career.
2026 Fall: I am hiring one PhD student and several funding-supported PhD students (need to PK university-wide), all with a scholarship of ~HK$19,500 per month. You can work on either LLM for Cybersecurity (any topic) or LLM Security/AI Safety.
For strong PhD applicants, I encourage you to try HKPFS. I also welcome international students for Belt & Road Scholarship.
I also look for one postdoc [28K-30K] or two RAs who understand (GPU) software security or (medical) system security.
Research Areas
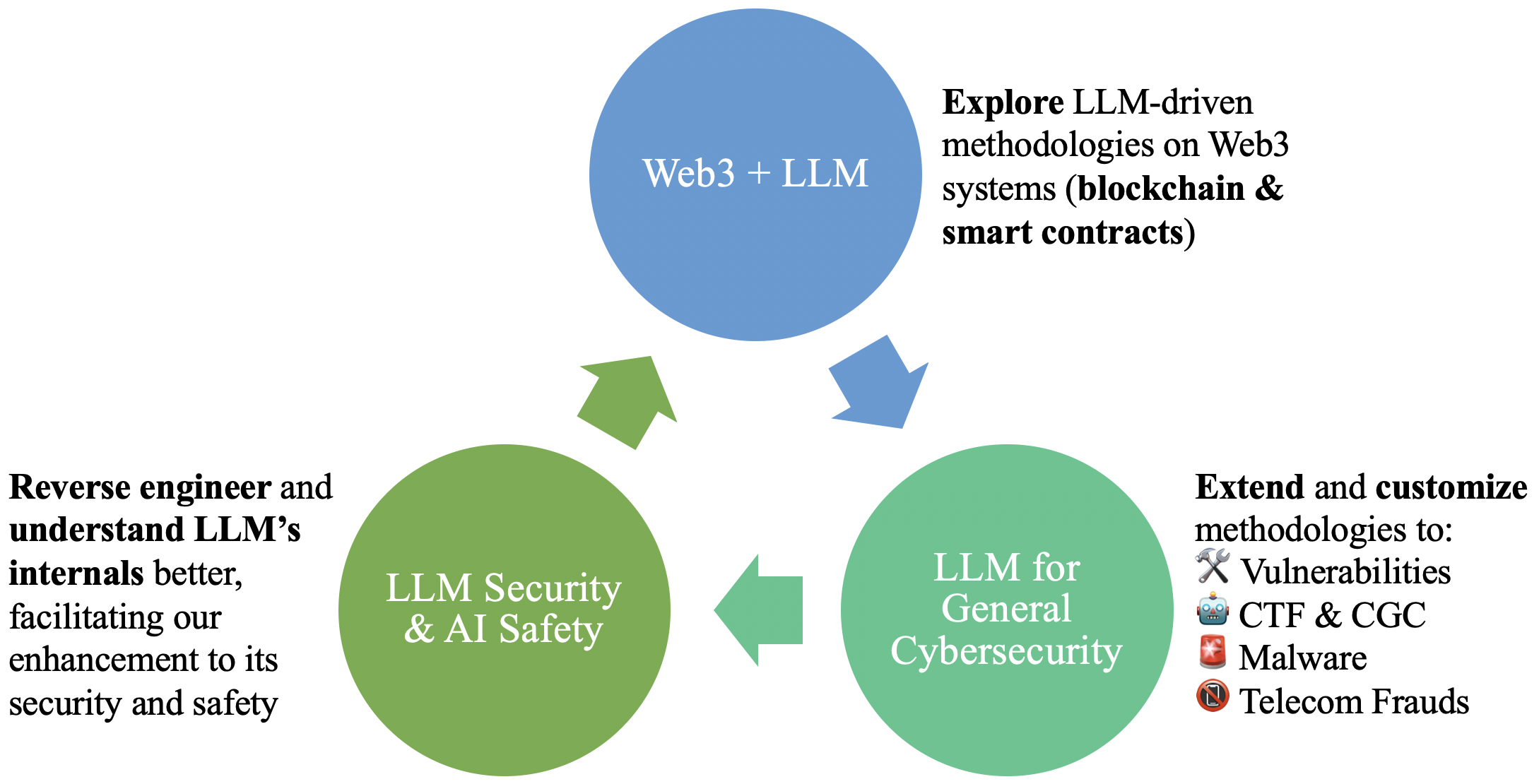
- RAG4Sec: LLM4Vuln, PropertyGPT, CTFAgent, ACFix, and MalwareGPT.
- Tune4Sec: iAudit, LLMImitation, DeFiScope, and MANDO-LLM.
- AISafety: SelfDefend, HEDiff, GuardRailSoK, GuidedBench, STShield.
- AgentSec: IPIDefenseSoK, MCPSecBench, PDoctor, MASLeak.
- LLMInternals: FinetuneDataExtraction, FC-Causality, BadMoE.
- LLM + Blockchain: GPTScan, BlockScope, ZepScope, ZepCompare, SoMo.
- LLM + Mobile/PL: CCF-Huawei System Fund 2025 🏆, BackDroid, MopEye.
- LLM + Software: G2Fuzz, DecLLM, and more.
- LLM + Law: ongoing.
-
Large Language Model and AI Security: LLMs for Cybersecurity; Security of LLMs; AI Safety.
AI/LLM4Sec: CTFAgent [CCS'25], G2Fuzz [USENIX'25], PropertyGPT [NDSS'25, 🏆], iAudit [ICSE'25], ACFix [TSE'25], DecLLM [ISSTA'25], GPTScan [ICSE'24; highly cited], PTM4AWI [TOSEM'25], LLM-SmartAudit [TSE'25], MANDO-LLM [TOSEM'25], ML4AWI [CSUR'24], SideNet [TII'21], MalwareGPT [arXiv'25], and LLM4Vuln [arXiv'24].
AI/LLM-Sec: GuardRailSoK [S&P'26], FinetuneDataExtraction [CCS'25], ConPETro [CCS'25], SelfDefend [USENIX'25], HEDiff [ICSE'25], LLMImitation [ICSE'24], FC-Causality [arXiv'25], GuidedBench [arXiv'25], STShield [arXiv'25], BadMoE [arXiv'25].
Agent-Sec: IPIDefenseSoK [arXiv'25], MCPSecBench [arXiv'25], MASLeak [arXiv'25], and PDoctor [arXiv'24].
AI/LLMQuality: DataScope [OOPSLA'25], Portia [EMNLP'24Main], MLM4VDL [arXiv'24], and VRPTEST [arXiv'23].
AI/LLM4Law: We are working on a very ambitious project related to LLM and law. Stay tuned for details.
AI/LLM4Edu: ContractTester [one UGC-funded TLIP grant] and iExam [two UGC-funded courseware grants]. -
Blockchain and Smart Contract Security: Chain & DeFi Security, Consensus Security, Transaction Compliance.
Blockchain: BlockScope [NDSS'23], MineBlockVuln [FSE'22], and AGChain [DLT'24; funded by CUHK Direct Grant].
Consensus: An ongoing work supported by a Blockchain Academic Research Award 🏆.
Contracts: ZepCompare [ASE'25], ACToolBench [ASE'25], PoCShift [ASE'25]. ZepScope [USENIX'24], and SoMo [ISSTA'23]. LLM-related are listed above.
Transactions: DeFiScope [ASE'25]. -
GPU Software and Medical System Security: AI Infrastructure Security; Healthcare and Medical Security; EdgeAI Security.
Mobile: MtdScout [EuroS&P'24], BackDroid [DSN'21; very creative tech, taking years of R&D], Insecure Open Ports [NDSS'19], DSDK Inconsistency [EMSE'21, WASA'17], Insecure PendingIntents [Blackhat Europe'21], IABI Usability Insecurity [RAID'21], VoIP Fuzzing [DIMVA'20], MineAndroVuln [AsiaCCS'19], SCLib [CODASPY'18], UpDroid [WiSec'18], Remote Webview [MoST'15], Local Webview File:// [ISC'14], App Repackaging [TDSC'21], Native Stack [ICISC'15], and ECVDetector [arXiv'14].
Software: TemuJs [OOPSLA'25] and LiCA [RAID'22]. LLM-related are listed above.
GPU Software: GGen [PLDI'25].
Medical System: Working on it. -
I am also interested in measuring mobile network performance and web privacy leaks.
MopEye [ATC'17], MopEye Dataset [IWQoS'19], Speedtest Inaccuracy [INFOCOM'15, TMC'17], and AcuteMon [CoNEXT'16].
Publications
Published Papers
Recent accepted papers will be shown first in https://ais2lab.github.io/publication/.
| P52 |
ACFix: Guiding LLMs with Mined Common RBAC Practices for Context-Aware Repair of Access Control Vulnerabilities in Smart Contracts TSE '25 ICSE '26 Journal-First |
| P51 |
Pre-trained Model-based Actionable Warning Identification: A Feasibility Study TOSEM '25 |
| P50 |
SoK: Evaluating Jailbreak Guardrails for Large Language Models S&P '26 |
| P49 |
Learning from the Past: Real-World Exploit Migration for Smart Contract PoC Generation ASE '25 |
| P48 |
Detecting Various DeFi Price Manipulations with LLM Reasoning ASE '25 |
| P47 |
Demystifying OpenZeppelin's Own Vulnerabilities and Analyzing Their Propagation in Smart Contracts ASE '25 |
| P46 |
Have We Solved Access Control Vulnerability Detection in Smart Contracts? A Benchmark Study ASE '25 |
| P45 |
Advanced Smart Contract Vulnerability Detection via LLM-Powered Multi-Agent Systems TSE '25 |
| P44 |
MANDO-LLM: Heterogeneous Graph Transformers with Large Language Models for Smart Contract Vulnerability Detection TOSEM '25 |
| P43 |
The Phantom Menace in Crypto-Based PET-Hardened Deep Learning Models: Invisible Configuration-Induced Attacks CCS '25 |
| P42 |
Measuring and Augmenting Large Language Models for Solving Capture-the-Flag Challenges CCS '25 |
| P41 |
Differentiation-Based Extraction of Proprietary Data from Fine-tuned LLMs CCS '25 |
| P40 |
Extraction and Mutation at a High Level: Template-Based Fuzzing for JavaScript Engines OOPSLA '25 |
| P39 |
API-guided Dataset Synthesis to Finetune Large Code Models OOPSLA '25 |
| P38 |
SelfDefend: LLMs Can Defend Themselves against Jailbreaking in a Practical Manner USENIX Security '25 |
| P37 |
Low-Cost and Comprehensive Non-textual Input Fuzzing with LLM-Synthesized Input Generators USENIX Security '25 |
| P36 |
Leakage-Resilient Easily Deployable and Efficiently Searchable Encryption (EDESE) SACMAT '25 |
| P35 |
DecLLM: LLM-Augmented Recompilable Decompilation for Enabling Programmatic Use of Decompiled Code ISSTA '25 |
| P34 |
Divergence-aware Testing of Graphics Shader Compiler Back-ends PLDI '25 |
| P33 |
Testing and Understanding Deviation Behaviors in FHE-hardened Machine Learning Models ICSE '25 |
| P32 |
Combining Fine-tuning and LLM-based Agents for Intuitive Smart Contract Auditing with Justifications ICSE '25 |
| P31 |
PropertyGPT: LLM-driven Formal Verification of Smart Contracts through Retrieval-Augmented Property Generation NDSS '25 🏆 |
| P30 |
AGChain: A Blockchain-based Gateway for Trustworthy App Delegation from Mobile App Markets DLT '24 |
| P29 |
Split and Merge: Aligning Position Biases in LLM-based Evaluators EMNLP '24 Main |
| P28 |
Machine Learning for Actionable Warning Identification: A Comprehensive Survey CSUR '24 |
| P27 |
Using My Functions Should Follow My Checks: Understanding and Detecting Insecure OpenZeppelin Code in Smart Contracts USENIX Security '24 |
| P26 |
MtdScout: Complementing the Identification of Insecure Methods in Android Apps via Source-to-Bytecode Signature Generation and Tree-based Layered Search EuroS&P '24 |
| P25 |
GPTScan: Detecting Logic Vulnerabilities in Smart Contracts by Combining GPT with Program Analysis ICSE '24 |
| P24 |
On Extracting Specialized Code Abilities from Large Language Models: A Feasibility Study ICSE '24 |
| P23 |
Beyond “Protected” and “Private”: An Empirical Security Analysis of Custom Function Modifiers in Smart Contracts ISSTA '23 |
| P22 |
BlockScope: Detecting and Investigating Propagated Vulnerabilities in Forked Blockchain Projects NDSS '23 |
| P21 |
An Empirical Study of Blockchain System Vulnerabilities: Modules, Types, and Patterns FSE '22 |
| P20 |
LiCA: A Fine-grained and Path-sensitive Linux Capability Analysis Framework RAID '22 |
| P19 |
On the Usability (In)Security of In-App Browsing Interfaces in Mobile Apps RAID '21 |
| P18 |
When Program Analysis Meets Bytecode Search: Targeted and Efficient Inter-procedural Analysis of Modern Android Apps in BackDroid DSN '21 |
| P17 |
Active Warden Attack: On the (In)Effectiveness of Android App Repackage-Proofing TDSC '21 |
| P16 |
Deep-Learning-Based App Sensitive Behavior Surveillance for Android Powered Cyber-Physical Systems TII '21 |
| P15 |
Scalable Online Vetting of Android Apps for Measuring Declared SDK Versions and Their Consistency with API Calls EMSE '21 |
| P14 |
Understanding Android VoIP Security: A System-level Vulnerability Assessment DIMVA '20 |
| P13 |
Towards Understanding Android System Vulnerabilities: Techniques and Insights AsiaCCS '19 |
| P12 |
An Empirical Study of Mobile Network Behavior and Application Performance in the Wild IWQoS '19 |
| P11 |
Understanding Open Ports in Android Applications: Discovery, Diagnosis, and Security Assessment NDSS '19 |
| P10 |
Towards Dynamically Monitoring Android Applications on Non-rooted Devices in the Wild WiSec '18 |
| P9 |
SCLib: A Practical and Lightweight Defense against Component Hijacking in Android Applications CODASPY '18 |
| P8 |
MopEye: Opportunistic Monitoring of Per-app Mobile Network Performance USENIX ATC '17 |
| P7 |
Toward Accurate Network Delay Measurement on Android Phones TMC '17 |
| P6 |
Measuring the Declared SDK Versions and Their Consistency with API Calls in Android Apps WASA '17 |
| P5 |
Demystifying and Puncturing the Inflated Delay in Smartphone-based WiFi Network Measurement CoNEXT '16 |
| P4 |
Stack Layout Randomization with Minimal Rewriting of Android Binaries ICISC '15 |
| P3 |
On the Accuracy of Smartphone-based Mobile Network Measurement INFOCOM '15 |
| P2 |
Indirect File Leaks in Mobile Applications MoST '15 |
| P1 |
Analyzing Android Browser Apps for file:// Vulnerabilities ISC '14 |
Technical Reports
| R16 |
Taxonomy, Evaluation and Exploitation of IPI-Centric LLM Agent Defense Frameworks arXiv '25 |
| R15 |
Digging Into the Internal: Causality-Based Analysis of LLM Function Calling arXiv '25 |
| R14 |
MCPSecBench: A Systematic Security Benchmark and Playground for Testing Model Context Protocols arXiv '25 |
| R13 |
Rethinking and Exploring String-Based Malware Family Classification in the Era of LLMs and RAG arXiv '25 |
| R12 |
IP Leakage Attacks Targeting LLM-Based Multi-Agent Systems arXiv '25 |
| R11 |
BadMoE: Backdooring Mixture-of-Experts LLMs via Optimizing Routing Triggers and Infecting Dormant Experts arXiv '25 |
| R10 |
STShield: Single-Token Sentinel for Real-Time Jailbreak Detection in Large Language Models arXiv '25 |
| R9 |
GuidedBench: Equipping Jailbreak Evaluation with Guidelines arXiv '25 |
| R8 |
Testing and Understanding Erroneous Planning in LLM Agents through Synthesized User Inputs arXiv '24 |
| R7 |
How Multi-Modal LLMs Reshape Visual Deep Learning Testing? A Comprehensive Study Through the Lens of Image Mutation arXiv '24 |
| R6 |
LLMs Can Defend Themselves Against Jailbreaking in a Practical Manner: A Vision Paper arXiv '24 |
| R5 |
LLM4Vuln: A Unified Evaluation Framework for Decoupling and Enhancing LLMs' Vulnerability Reasoning arXiv '24 |
| R4 |
VRPTEST: Evaluating Visual Referring Prompting in Large Multimodal Models arXiv '23 |
| R3 |
iExam: A Novel Online Exam Monitoring and Analysis System Based on Face Detection and Recognition arXiv '22 |
| R2 |
MopEye: Monitoring Per-app Network Performance with Zero Measurement Traffic CoNEXT '15 Poster |
| R1 |
A Sink-driven Approach to Detecting Exposed Component Vulnerabilities in Android Apps arXiv '14 |
Invited Talks
| T10 |
Web3 + LLM: The Road Toward Secure and Smart Web3 SYSY Seminar '24 |
| T9 |
Discovering and Investigating Propagated Vulnerabilities from Ethereum to Its Layer-2 Blockchains HITBSecConf '24 |
| T8 |
构建基于大模型的智能漏洞审计引擎 AI Con HK 2024 |
| T7 |
Proof-of-Work vs. Proof-of-Stake: Insights into Fairness and Governance Sustainability from the Blockchain World Business Sustainability Conference '23 |
| T6 |
Re-route Your Intent for Privilege Escalation: A Universal Way to Exploit Android PendingIntents in High-profile and System Apps Blackhat Europe '21 |
| T5 |
Leveraging Automatic Face Recognition for Online Exam Monitoring and Analysis CUHK Expo '21 |
| T4 |
Boosting Android Security through App-, Network-, and System-level Vulnerability Analysis NJUPT Keynote '19 |
| T3 |
On-device Crowdsourcing and Bytecode Search for Advancing Android App Analysis HKBU Seminar '19 |
| T2 |
Cross-Platform Analysis of Indirect File Leaks in Android and iOS Applications HitCon Pacific '17 |
| T1 |
On the Feasibility of Automatically Generating Android Component Hijacking Exploits HitCon '14 |
Teaching
-
2026 Spring - CCC8015 Generative Artificial Intelligence: Lab (CRN: 192; within LU).
-
2025 Fall - CCC8015 Generative Artificial Intelligence: Lecture (CRN: 188; within LU) and Lab (CRN: 190; within LU).
-
2025 Fall - CDS701 Fundamentals of Computer Science: English track (CRN: 3098) and Chinese track (CRN: 3099).
-
2025 Spring - COMP4541 Blockchain, Cryptocurrencies and Smart Contracts: homepage (within UST) and mirror website.
-
2022 Fall - IEMS5710 Cryptography, Information Security and Privacy: homepage (within CUHK) and mirror website (public).
-
2021 Fall - IERG4130 Introduction to Cyber Security: homepage (within CUHK) and mirror website (public).
-
Received the Best Teaching Award of the MScIE Programme 2020-2021.
-
2021 Spring - IEMS5722 Mobile Network Programming and Distributed Server Architecture: homepage and mirror website.
-
2020 Fall - IEMS5710 Cryptography, Information Security and Privacy: homepage (within CUHK) and mirror website (public).
-
2019 Fall - IEMS5710 Cryptography, Information Security and Privacy: homepage (within CUHK) and mirror website (public).
2026 Spring - CCC8015 Generative Artificial Intelligence: Lab (CRN: 192; within LU).
2025 Fall - CCC8015 Generative Artificial Intelligence: Lecture (CRN: 188; within LU) and Lab (CRN: 190; within LU).
2025 Fall - CDS701 Fundamentals of Computer Science: English track (CRN: 3098) and Chinese track (CRN: 3099).
2025 Spring - COMP4541 Blockchain, Cryptocurrencies and Smart Contracts: homepage (within UST) and mirror website.
2022 Fall - IEMS5710 Cryptography, Information Security and Privacy: homepage (within CUHK) and mirror website (public).
2021 Fall - IERG4130 Introduction to Cyber Security: homepage (within CUHK) and mirror website (public).
Received the Best Teaching Award of the MScIE Programme 2020-2021.
2021 Spring - IEMS5722 Mobile Network Programming and Distributed Server Architecture: homepage and mirror website.
2020 Fall - IEMS5710 Cryptography, Information Security and Privacy: homepage (within CUHK) and mirror website (public).
2019 Fall - IEMS5710 Cryptography, Information Security and Privacy: homepage (within CUHK) and mirror website (public).
Collaborators
(Only faculty members with whom I have recent HotCRP conflicts are listed.)Singapore:
-
Chair Prof. Yang Liu (hosted my Senior Research Fellow position at NTU); Prof. Debin Gao (my PhD advisor); Chair Prof. Robert Deng (my PhD co-advisor); Prof. Lingxiao Jiang; Assoc Prof. Yi Li; Assoc Prof. Shang-Wei Lin; Asst Prof. Xiaofei Xie.
Hong Kong SAR:
-
Assoc Prof. Shuai Wang (hosted my RAP position at UST, with support from university’s matching fund); Assoc Prof. Ning Liu; Prof. Guoliang Xing; Prof. Kehuan Zhang; Prof. Xiapu Luo (my MPhil co-advisor at PolyU); Prof. Wei Lai; Assoc Prof. Yanzhen Chen; Chair Prof. Shing-Chi Cheung; Chair Prof. Jianliang Xu; Prof. Jimmy Lee; Prof. Tan Lee.
USA:
-
Prof. Rocky K. C. Chang (my MPhil advisor at PolyU, who has retired and is now based in the US); Ripple Prof. Yingjiu Li; Prof. Jun Li; Assoc Prof. Ricky K. P. Mok; Research Asst Prof. Hoang H. Nguyen.
Mainland China:
-
Prof. Jiachi Chen; Prof. Bin Zhang; Assoc Prof. Han Liu; Assoc Prof. Haoyu Ma; Assoc Prof. Weichao Li; Assoc Prof. Zhiyuan Wan; Assoc Prof. Xiuting Ge; Prof. Wei Zhang; Prof. Haijun Wang; Prof. Cuiyun Gao; Prof. Jianting Ning; Prof. Xin Xia; Assoc Prof. Lingfeng Bao; Prof. Zhong Chen; Prof. Ting Chen; Prof. Shaohua Wang; Prof. Liehuang Zhu; Prof. Zijian Zhang; Prof. Zhenyu Chen; Prof. Zhihong Zhao; Assoc Prof. Chunrong Fang; Asst Prof. Yanlin Wang; Asst Prof. Wenxuan Wang; Asst Prof. Yuanyuan Yuan; Prof. Ye Liu; Prof. Pingchuan Ma; Prof. Zhibo Liu; Prof. Huaijin Wang; Assoc Prof. Jian Zhang; Assoc Prof. Shangqing Liu.
Europe & Other Regions:
-
Prof. Zhendong Su; Asso Prof. Lei Ma; Asso Prof. Jing Sun; Asst Prof. Yangguang Tian; Asst Prof. Haoye Tian.
Professional Services
Conference Program Committee:
-
CCS 2026 (Blockchain track), USENIX Security 2026, NDSS 2026, ICML 2026, ICLR 2026, AAAI 2026, ICME 2026, ACNS 2026, CCS 2025 (Blockchain track), USENIX Security 2025, NDSS 2025, ICSE 2025, ISSTA 2025, CCS 2024 (Software track), ACSAC 2024, RAID 2024, AsiaCCS 2024, ICICS 2024, RAID 2023, ICICS 2023, ICICS 2021, and NOMS 2018.
Conference Shepherd:
-
USENIX Security 2025 (for this paper), NDSS 2025 (for this paper), CCS 2024 (for this paper), RAID 2023 (for this paper), and ICICS 2021 (for this paper).
Journal Editorial Board:
-
Youth Editorial Board Member at Cybersecurity (July 2025 to July 2027).
Journal Reviewer:
-
Top Journals: PNAS, PNAS Nexus.
-
ACM Transactions on Privacy and Security, ACM Transactions on Software Engineering and Methodology, IEEE Transactions on Information Forensics and Security, IEEE Transactions on Dependable and Secure Computing, IEEE Transactions on Software Engineering, IEEE Transactions on Pattern Analysis and Machine Intelligence, IEEE Transactions on Mobile Computing, Cybersecurity, Journal of Systems and Software, Journal of Information Security and Applications, IEEE Systems Journal, ACM Distributed Ledger Technologies, IEEE Journal of Selected Topics in Applied Earth Observations and Remote Sensing, etc.
Workshop Program Committee:
-
SVM 2025 (co-located with ICSE 2025) and AISTA 2024 (co-located with ISSRE 2024).
Useful Links
My calendar of security conferences: academia and industry. Recently used: CCF Conference Deadlines.
I was maintaining a list of interesting computer security papers and a list of mobile app related software engineering papers.
Security Journals: TIFS (special issues), TDSC (special issues), Computers & Security (special issues), TISSEC, and JCS.
Top Journals (our next targets): Nature Communications, PNAS, Science, and Nature.
Storytelling 101: Writing Tips for Academics (by Nick Feamster).
Top Publication Venues in Computer Science (by Andrew Myers).
ArnetMiner CS Rank: conference rank and organization rank.
CCF Conference and Journal Rankings: AI, Security, Networking, System, and Software Engineering.
Google Scholar Metrics in AI, Computer Security, Computing Systems, Computer Networks, and Software Systems.
My calendar of security conferences: academia and industry. Recently used: CCF Conference Deadlines.
I was maintaining a list of interesting computer security papers and a list of mobile app related software engineering papers.
Security Journals: TIFS (special issues), TDSC (special issues), Computers & Security (special issues), TISSEC, and JCS.
Top Journals (our next targets): Nature Communications, PNAS, Science, and Nature.
Storytelling 101: Writing Tips for Academics (by Nick Feamster).
Top Publication Venues in Computer Science (by Andrew Myers).
ArnetMiner CS Rank: conference rank and organization rank.
CCF Conference and Journal Rankings: AI, Security, Networking, System, and Software Engineering.
Google Scholar Metrics in AI, Computer Security, Computing Systems, Computer Networks, and Software Systems.